Our Training Development Process (TDP) is a continuous, skills-based framework designed to keep teams sharp, confident, and ready under pressure. Built around a structured lifecycle, it ensures your people don’t just train, they learn, apply, and evolve in alignment with your business objectives and real-world challenges.
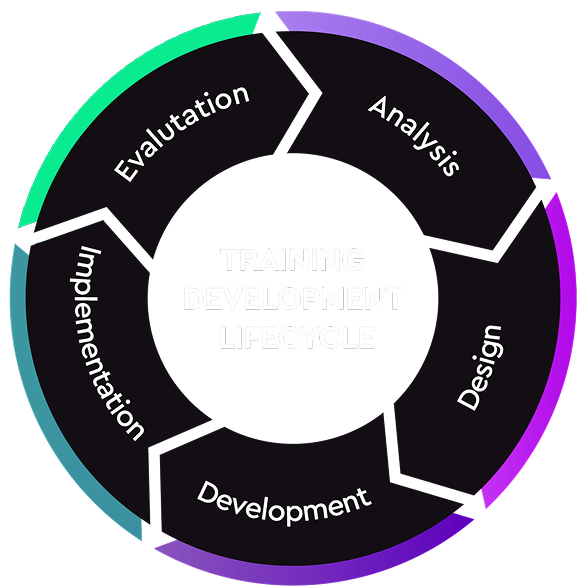
Training shouldn’t end when the course does. Our lifecycle approach embeds learning into your organization’s performance model, from identifying skill gaps to evaluating impact on real operations.
We deliver training that is systematic, measurable, and business-impact driven, helping organizations turn learning into lasting operational readiness.
1
2
3
Create tailored materials, labs, and exercises based on the organization’s technical ecosystem and security environment. All resources are designed to mirror real-world conditions and reinforce practical application.
4
Execute training through the chosen delivery model. Incorporate live instruction, simulations, and progress tracking to ensure consistent engagement and measurable skill development.
5
Measure training effectiveness and operational impact through structured performance measurement and ROI analysis. Quantify impact, evaluate skill gains, and link results to operational readiness. Adapt content, update delivery, and refine training as needs evolve.
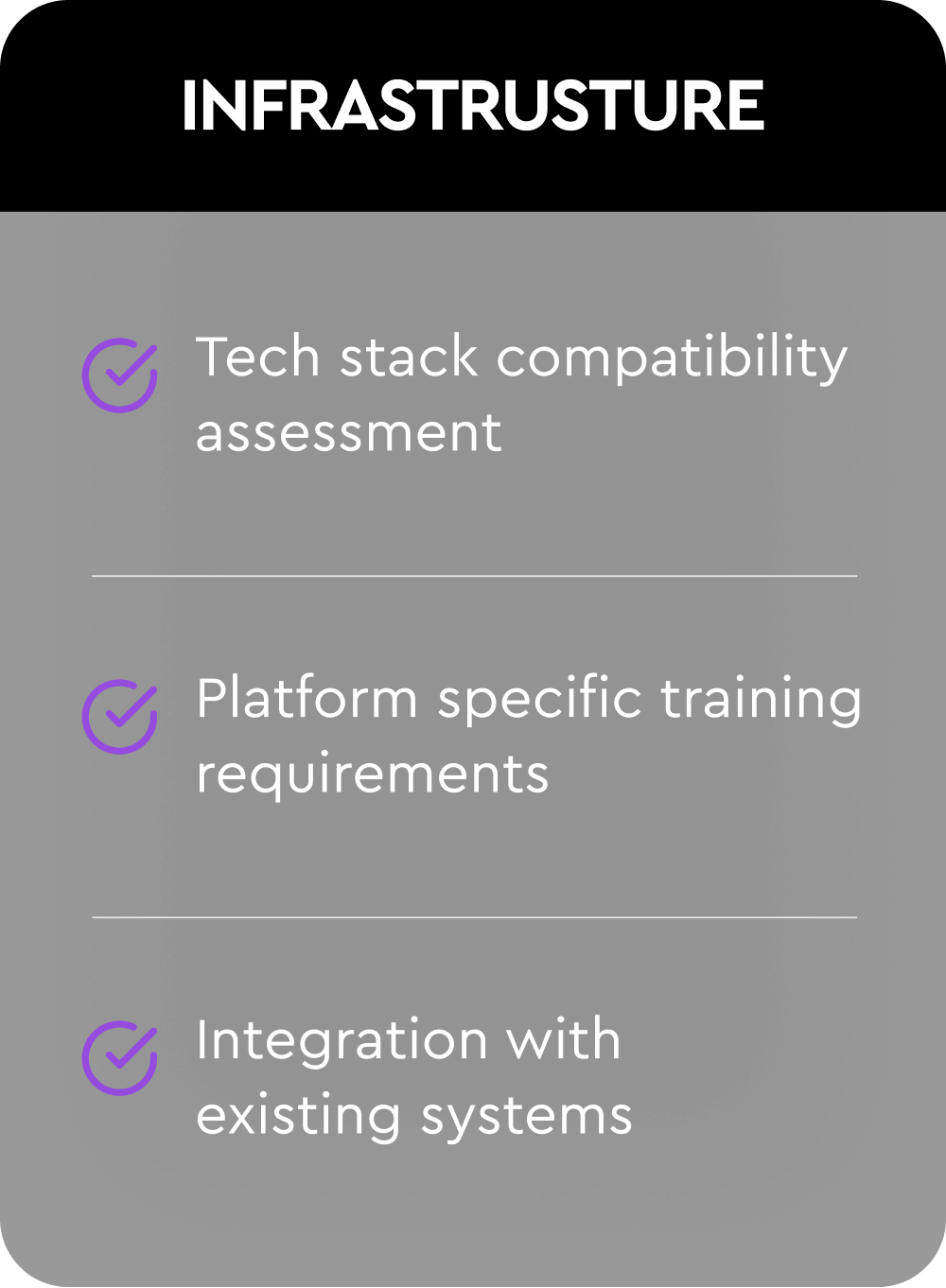
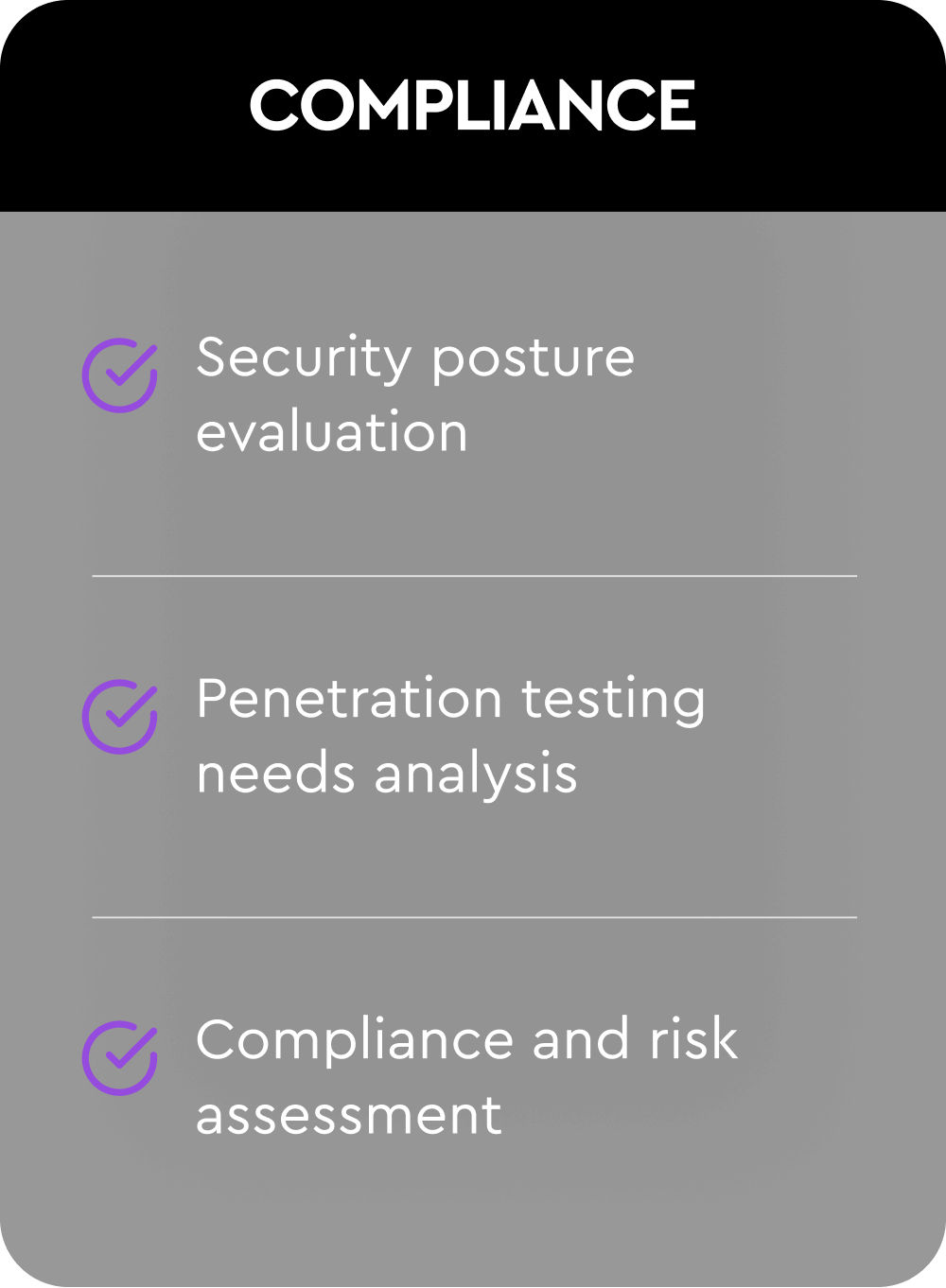
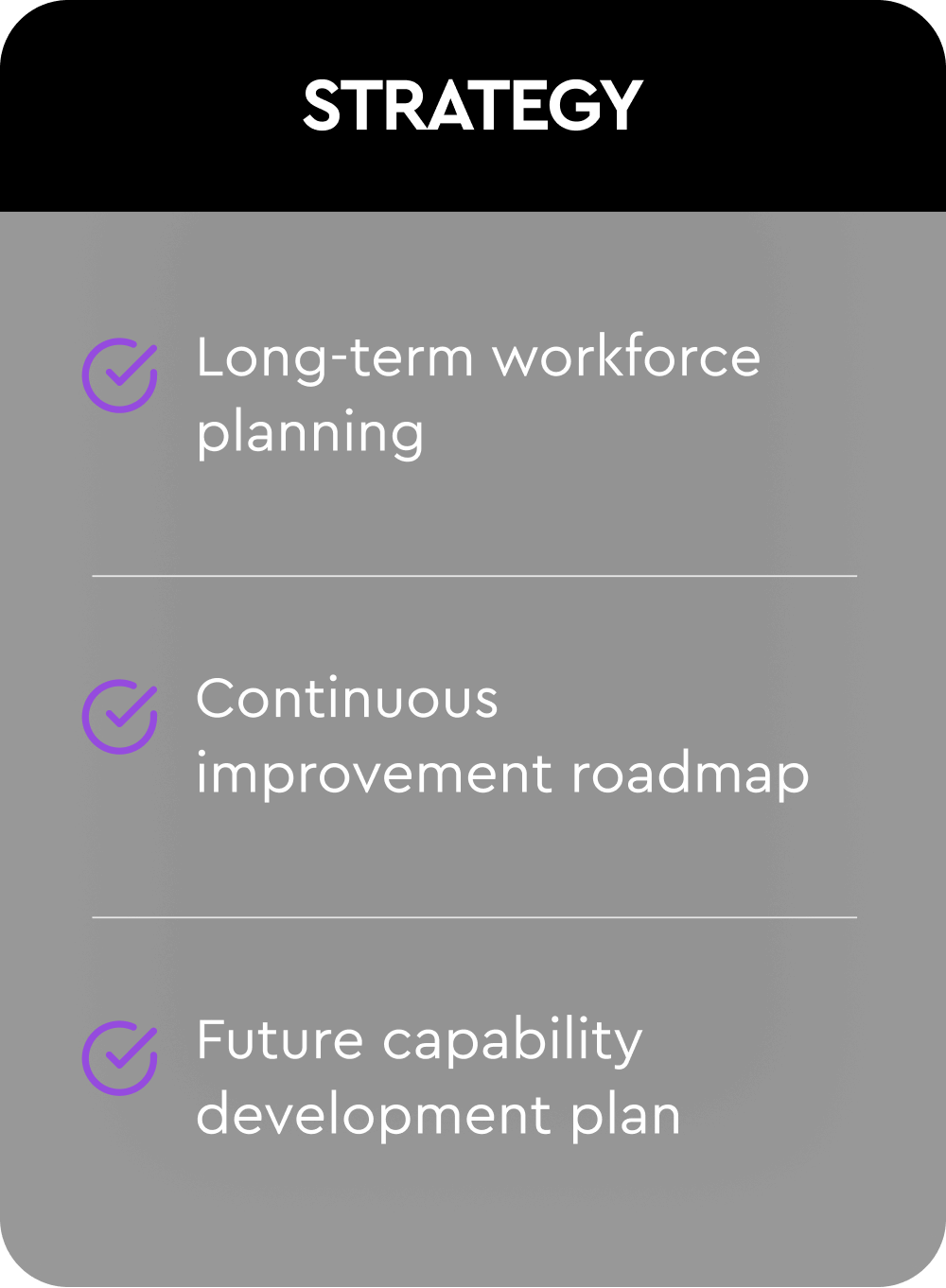
A five-pillar framework designed to deliver a holistic, actionable evaluation of your organization’s cybersecurity readiness.



To provide the best experiences, we and our partners use technologies like cookies to store and/or access device information. Consenting to these technologies will allow us and our partners to process personal data such as browsing behavior or unique IDs on this site and show (non-) personalized ads. Not consenting or withdrawing consent, may adversely affect certain features and functions.
Click below to consent to the above or make granular choices. Your choices will be applied to this site only. You can change your settings at any time, including withdrawing your consent, by using the toggles on the Cookie Policy, or by clicking on the manage consent button at the bottom of the screen.
Syllabus:
Intro to GCP
Exploitation of GCP Services
Methodologies
Security Services
Syllabus:
Intro to AWS
Exploitation of AWS Services
Methologies
Common Detection Mechanisms
Syllabus:
Azure Basics
Exploitation of Azure Services
Methologies
Common Detection Mechanisms
Fundamentals and Setup
Advanced Techniques and Practical Application
Advanced Techniques and Practical Application
Fundamentals & Setup